COMP4801Owl: Automatically identifying and avoiding concurrency attacks
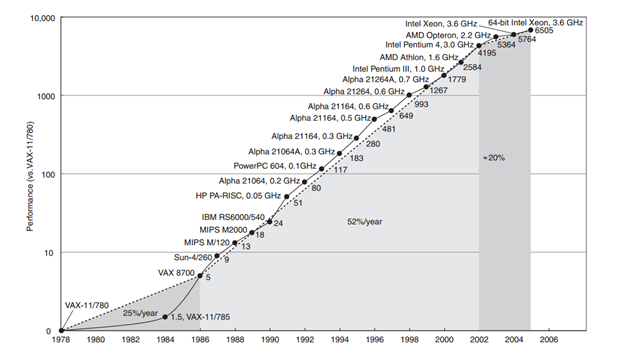
COMP4801Owl: Automatically identifying and avoiding concurrency attacksThe rise of computing power over years in the form of multiple core machines with powerful processors supporting distributed systems has entailed programmers to use it. Thus, there has been a surge in multithreaded programs. Multithreading is a technique that allows the code to use more than one processor and thus executing its parts simultaneously and hence faster. Figure 1 below shows the increase in computing power since 1980s in comparison to VAX-11/780 according to SPECint benchmarks. Just as errors in sequential programs incur security issues, errors in multithreaded programs do as well. The fact that multithreaded programs are hard to get right in the first place increases the vulnerability. The attacks on multithreaded programs are called Concurrency attacks and violate integrity, confidentiality and the availability of the systems. Therefore, there is a strong need to avoid such attacks. The exploitability of a concurrency error depends on the duration of the timing window within which the error are likely to happen. Moreover, certain inputs can increase this window which increases the exploitability. Most researchers and security specialists have worked on sequential programs, however, four out of five most commonly used security techniques used for sequential programs fail to defend against concurrency attacks. Even the most famous softwares are vulnerable e.g. Windows, MacOS X, Linux, and Apple iOS, including kernels such as the Linux, system libraries such as GNU Libc, and user-space programs such as KDE, Apache and Chrome. Thus there is a clear need for mechanisms and tools to detect and avoid these attacks.