FYP 17059
Han Yu
Supervisor: Dr. S. M. Yiu
In the challenge, users are needed to choose the best monkey, with ideal name, IQ and body strength as shown in figure 22. And there is a file named monkey name list provided and users are expected to try all the name inside this file.

Each time the superman picture is clicked or the page is refreshed, a new set of body condition parameters will be presented.
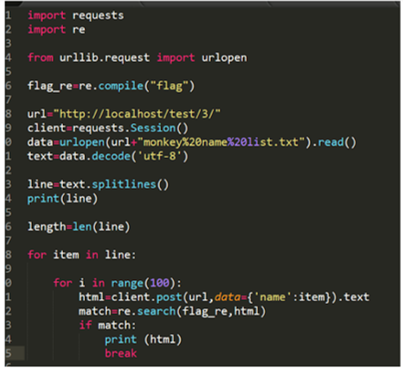
There is a file called monkey name list which contains many possible monkey names.
Only if the bofy conditions macth full marks and are paired with the proper monkey name, can the hackers get the flag.
In this case, a pyhton script is used to send multiple HTTP requests to the servers and sereach for matching cases. The following is the sample solution written in python3.