Intoduction
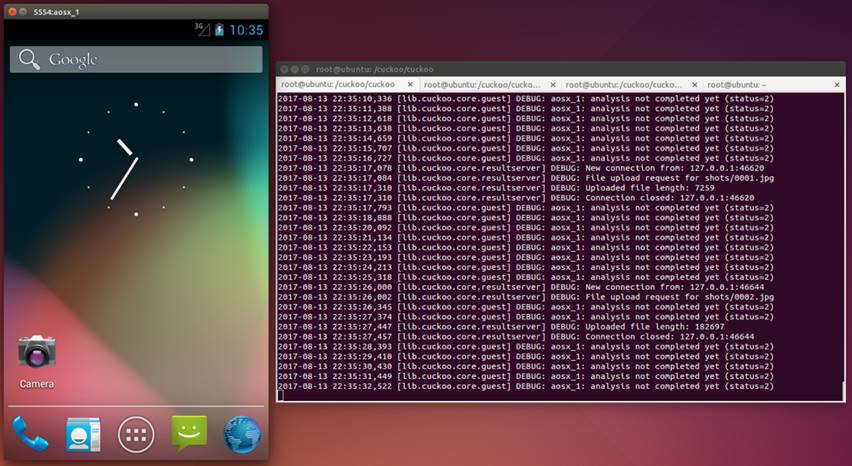
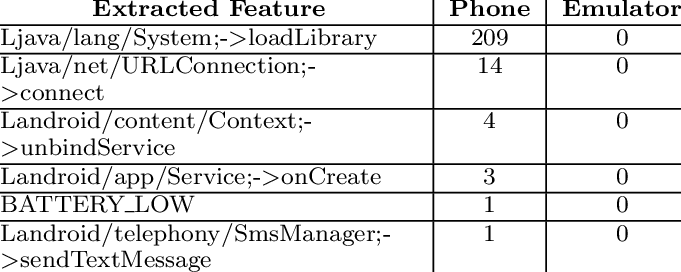
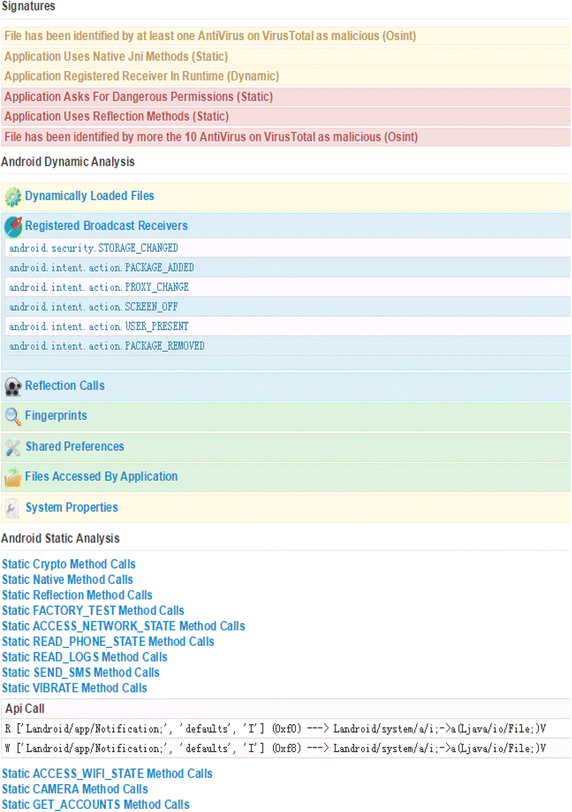
Until now, Android is still the most popular mobile framework. Concurrently, the history tells us Android is also a malware nest due to its high market occupation. In addition, the amount of malware is numerous. Therefore machine learning is probably the trend for malware detection. In fact, when we apply machine learning to classify the samples, apart from signature extraction and matching, dynamic analysis is sometimes an option for extracting more features from samples to improve the overall accuracy. Since dynamic analysis is using emulators to test the sample, if the samples can detect emulator properties, they will not do anything. As a result, the dynamic analysis fails to detect the malware behavior according to this kind of anti-analysis technique. In practice, dynamic analysis is hard to provide useful information for classifying the samples.