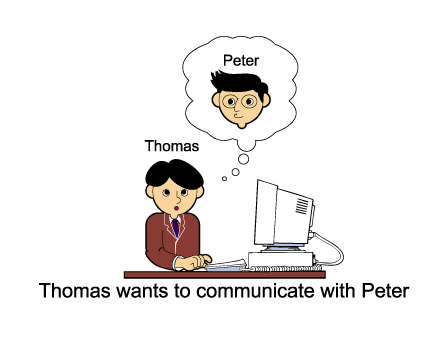
We are going to study the data encryption example in more details. This illustrates the key management issues for Public Key Crypto-Systems. Suppose Thomas wants to send a secret message to Peter. He can do that without keeping Peter's public key.
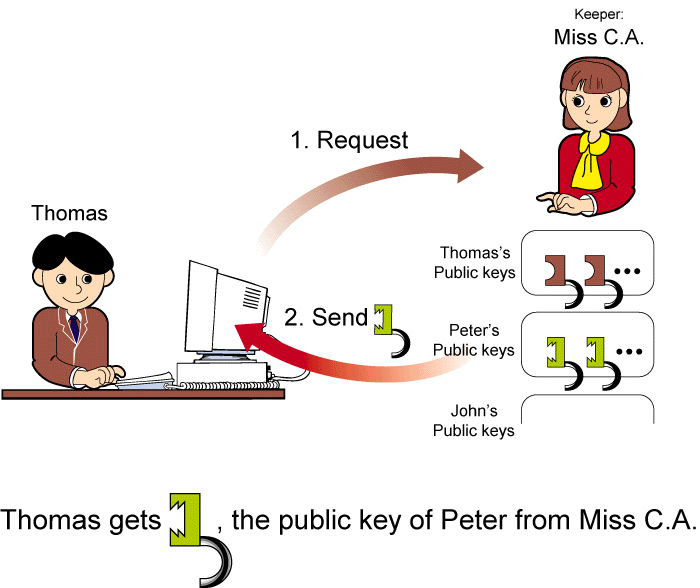
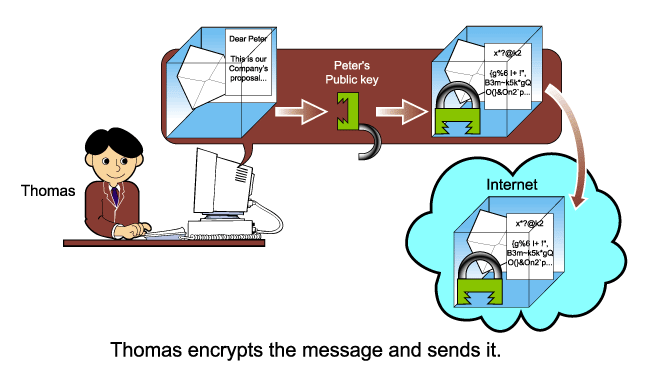
Then Thomas encrypts the message with Peter's public key. Note that this encrypted message can ONLY be decrypted by Peter's private key. Thomas then sends the encrypted message via the Internet.
After Peter receives the encrypted
message from the Internet, he uses his own private key to decrypt it.
The same public key can be used by others to send secret messages to Peter.
Note that for the whole system
to work, there are two important key management issues: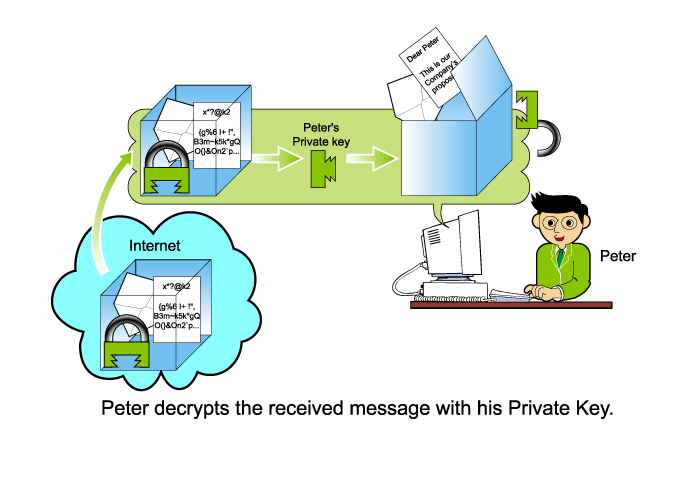
|
|