
Digital signature
using Public Key Crypto-System
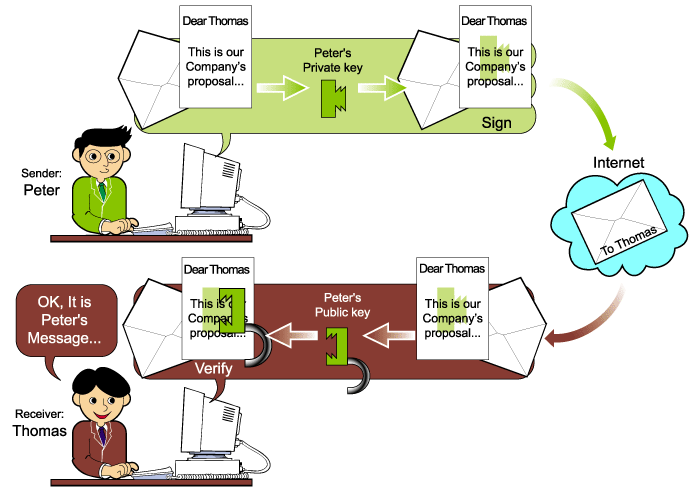
Suppose Peter wants to send his signed
message to Thomas via Internet, he can use the Public Key Crypto-System to provide
digital signatures. Peter uses his own private key to produce a digital
signature. Thomas will use Peter's public key to verify this digital signature.
A digital signature is different from a hand-written signature. Usually,
a digital signature is an encrypted item.
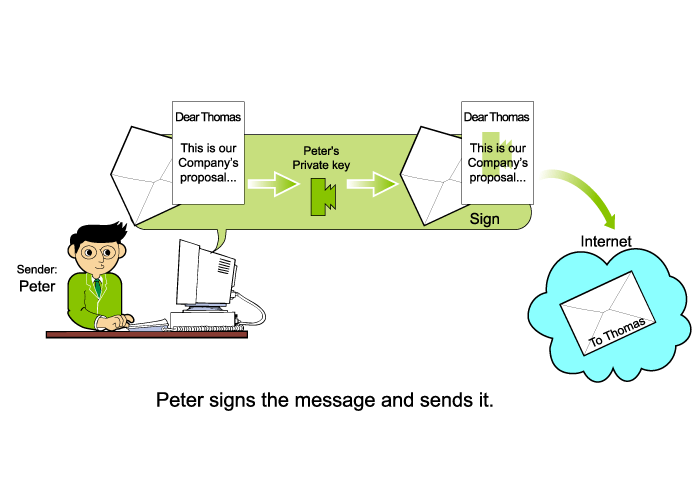
The
digital signature generation process is as follows:
Peter uses his private
key to generate the digital signature. Technically it is the same as
"encrypting" the messages with Peter' private key, and the result after encryption
is the signed message.
Peter sends signed message
to Thomas via the Internet.
Note that the digital signature
can only be generated by Peter's private key. Technically, if the message
is modified, the digital signature will be different.
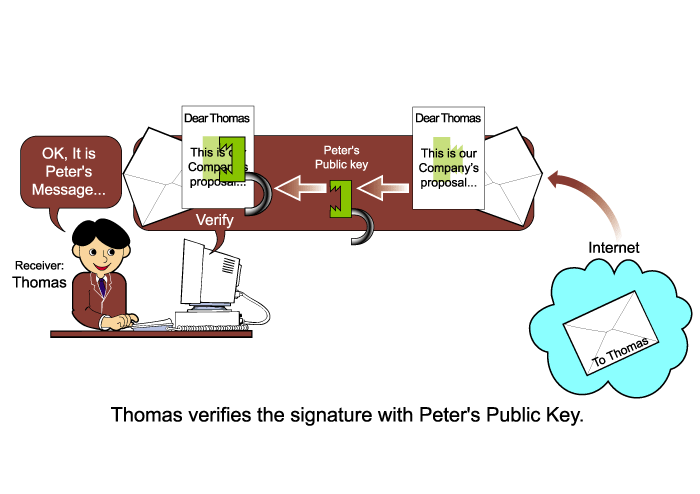
The digital
signature verification process is as follows:
Thomas receives the message,
together with the digital signature from the Internet.
Thomas gets a copy of
Peter's public key from Miss C.A.
Thomas will verify the
signature by Peter's public key. Technically, Thomas "decrypts" the
message with Peter's public key. If the result after decryption is the
same as the transmitted message, Thomas can believe that the message is really
come from Peter. This is because only Peter holds his private key, which
is needed to generate the digital signature.
Therefore, Peter cannot
deny that he sends this message to Thomas.
 Note that if the message or
the digital signature is modified during the transmission, Thomas will not find
the "decrypted" digital signature matches the message, then Thomas can conclude
that either the message transmission is tampered, or the message is not generated
by Peter.
Note that if the message or
the digital signature is modified during the transmission, Thomas will not find
the "decrypted" digital signature matches the message, then Thomas can conclude
that either the message transmission is tampered, or the message is not generated
by Peter. The key management
issues are similar to sending secret message:
User needs to protect
his/her private key really secret.
User's public key has
to be known correctly by all other people. If Thomas gets a wrong copy
of Peter's public key, he will wrongly accept a message signed by somebody
else as being signed by Peter.
Chinese Version
Copyright
© 1999 Department of Computer Science and Information Systems, The University
of Hong Kong. All rights reserved.


