Blockchain Research and Implementation
Research on Ethereum Smart Contracts Security Vulnerabilities & Web-based Checking ToolNG King Pui UID: 3035178820
Supervised by Dr S.M. Yiu
Project Background
Blockchain is a hot topic in the technology world. One of the applications with great impact to different sectors is smart contracts on Ethereum chain. However, there are still various security vulnerabilities in smart contracts. In this project, the aim is to study these security vulnerabilities, and to develop a simple web-based checking tool to detect if such security vulnerabilities exist in smart contracts.
Security Vulnerabilities
DAO Attack
The checking mechanism is bypassed by the the unknown states of contracts. Contract may emptied.
Short Address Attack on ERC20 Tokens
The hacker passes in a shorter address, which is still valid as it is trailed with 0. Then the EVM will fill the missing bytes by 0, which makes the value to transfer larger than expected value.
DoS by Calling to the Unknowns
The hacker writes another contract which will always refuse to receive Ether. When the contract under attack tries to send Ether to it, it will always fail and the later lines are not called, stopping the service to a certain extent.
Delegate Call
The hacker can abuse this loophole to claim unauthorized ownership of a contract, which further leads to other dishonest behaviour.
Forcing Ether
The hacker can forcefully transfer Ether to a contract by self-destorying itself. This can bypass the checking mechanism of contracts' balance.
Uint Overflow/ Underflow
The value of numerical variables may be out of expectation if unit overflow/ underflow is not properly handled.
Web-based Checking Tool
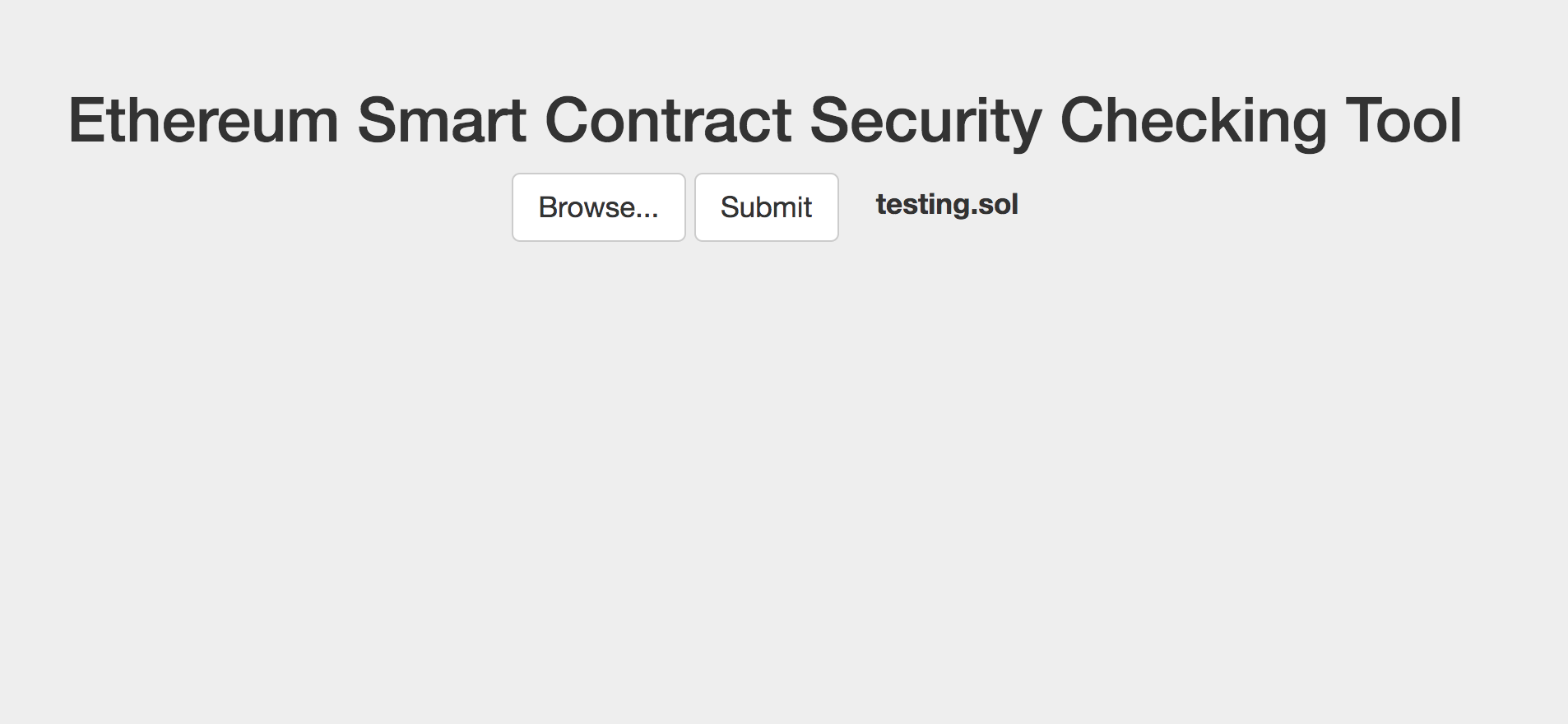
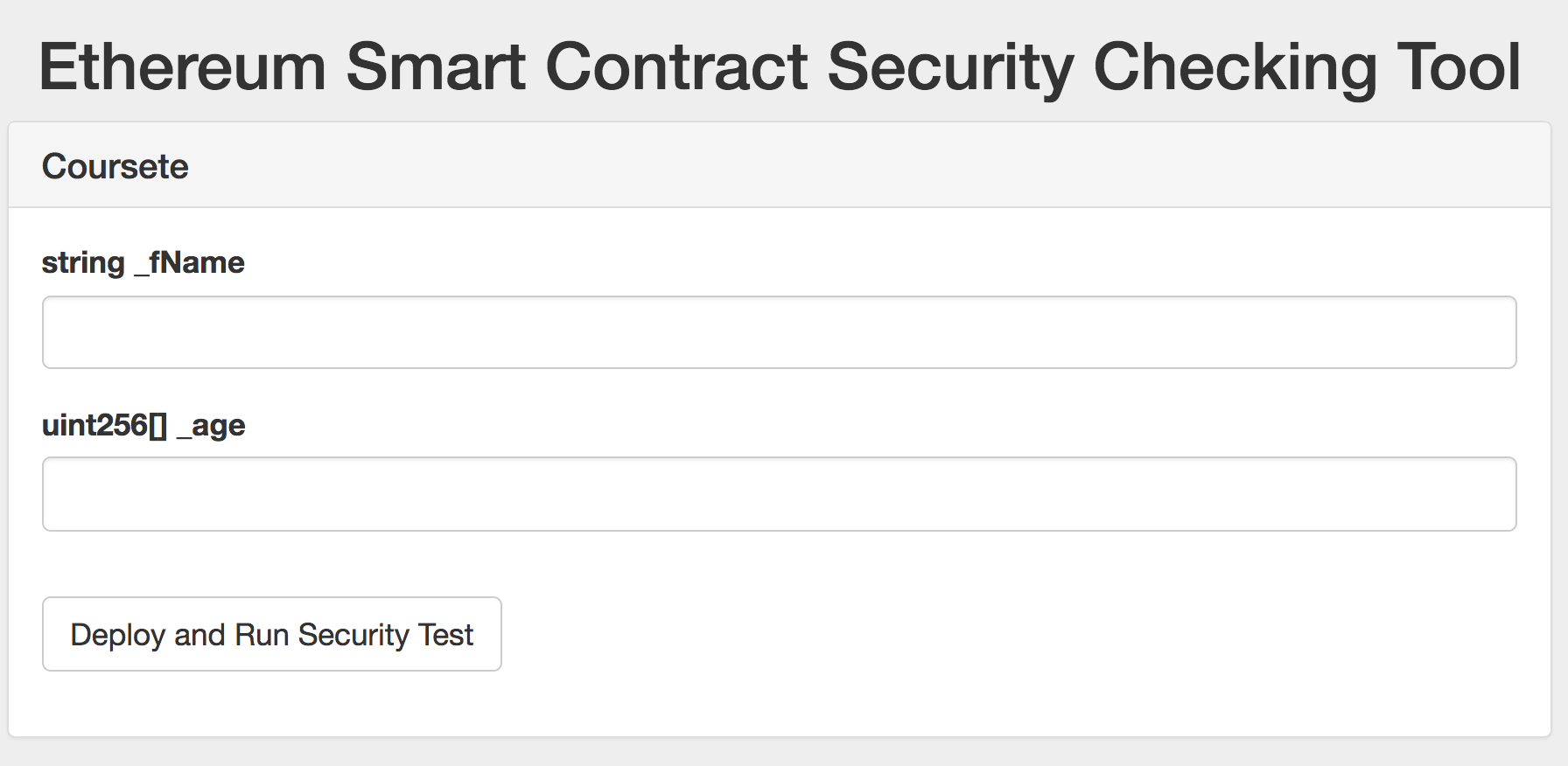
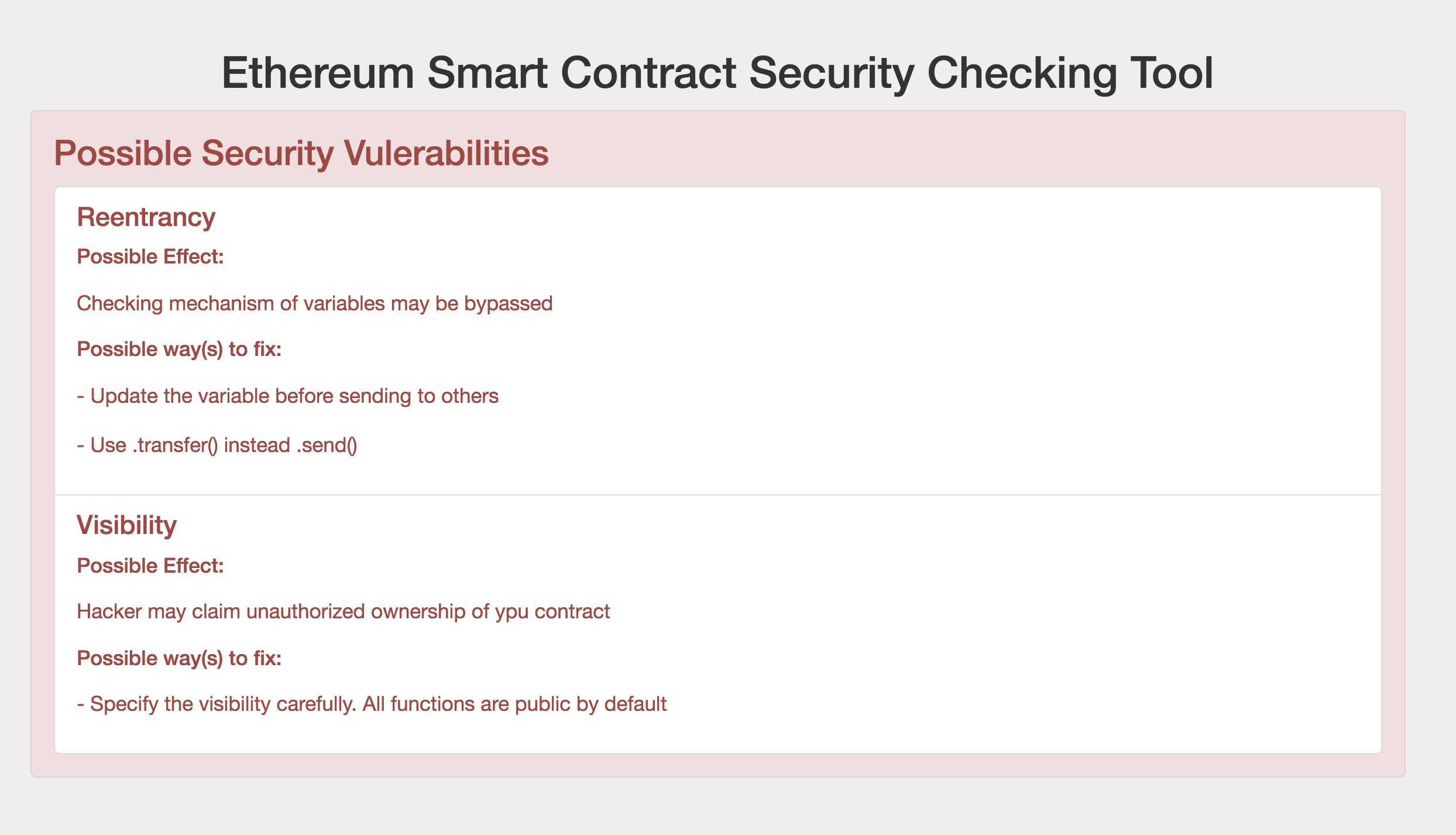
Users can upload their smart contracts files to the tool and a brief security report with possible effects and recommended ways to fix is returned for reference after checking.